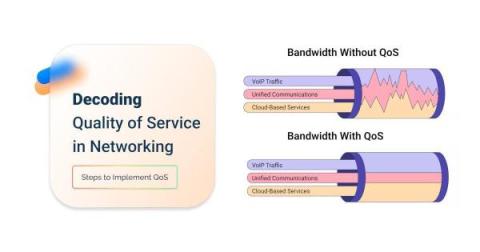
Coralogix vs Observe: Support, Pricing, Features & More
Observe is a SaaS based observability tool built on Snowflake. It offers a graph-style approach to observability data, claiming that this makes it easier to correlate data in a seamless fashion. Let’s see how Observe compares to Coralogix.