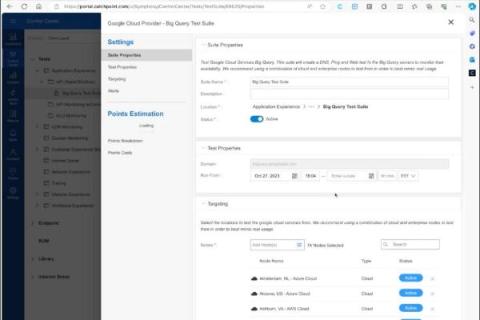
Google Test Suite: Monitoring Google Cloud Services Just Got Easier
In today's dynamic cloud computing environment, effective monitoring of cloud services is essential. Developed in partnership with Google Cloud, Google Test Suite offers easy-to-deploy test templates to monitor your Google Cloud Platform (GCP) services.