Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
Release Roundup Dec 2023: Driving reliability standards (and much more)
The Advent of Monitoring, Day 6: How We Use Checkly to Monitor Checkly: A Backender's Perspective
Table of contents As a golden rule of building a developer tool, you should always dog-food your own product. But, how does this work with a monitoring solution 🤔? Doesn’t it create a chicken and egg problem? Checkly uses multiple tools to monitor the platform, and tools from our competitors as well. However, we still dogfood our platform heavily. I believe this is mainly due to our engineers also liking the product and finding it quite easy to monitor their features.
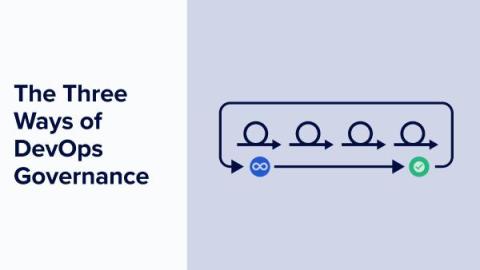
The Three Ways of DevOps Governance
In this blog post, I take a look at modern IT governance by applying the classic “Three Ways” of DevOps principles originally introduced by Gene Kim in his seminal 2012 article. “We assert that the Three Ways describe the values and philosophies that frame the processes, procedures, practices of DevOps, as well as the prescriptive steps.” Here’s a quick reminder of the three ways set out by Gene: For Gene, all DevOps patterns can be derived from these three principles.
Network Observability 101: A Primer
In today's digital-first landscape, maintaining the health and performance of your network is critical for the seamless operation of your business and its services. To that end, network observability has emerged as a key concept and discipline in ensuring the robustness and performance of networks. But what is network observability?
5 Ways AIOps Monitoring Benefits EUC Environments
The adoption of AIOps monitoring technologies has been somewhat slower in EUC than many other areas of IT. The legacy VDI and DaaS vendor tools set expectations low for many. It is still relatively common for us to come across potential customers who are using legacy tools and manually exporting 6 months of data into an excel spreadsheet to try and work out average and peak usage of resources such as CPU to then manually calculate alert thresholds.
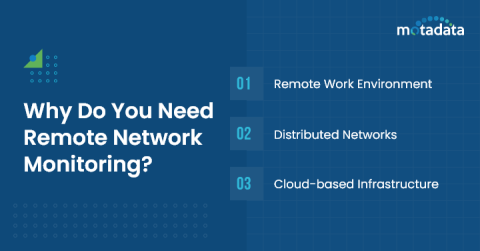
Top 9 Benefits of Remote Network Monitoring
Are you relying on outdated manual methods to monitor your network? Struggling to keep up with the increasing complexity of your IT infrastructure? Being constantly reactive to network problems instead of proactive in preventing them? If you answered yes to any of these questions, then you’re putting your business at risk. But don’t worry, there’s a way out — Remote Network Monitoring.
Five reasons why every CIO should consider Kubernetes
You should read this if you are an executive (CIO/CISO/CxO) or IT professional seeking to understand various Kubernetes business use cases. You’ll address topics like: Many enterprises adopting a multi-cloud strategy and breaking up their monolithic code realize that container management platforms like Kubernetes are the first step to building scalable modern applications.