How to Perform a Forensic Analysis After a Security Breach
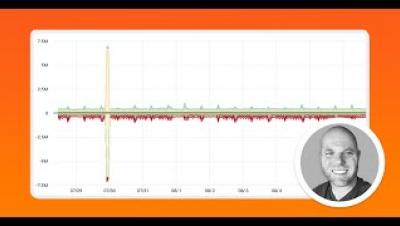
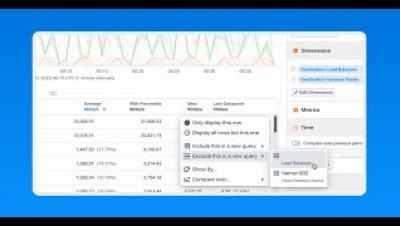
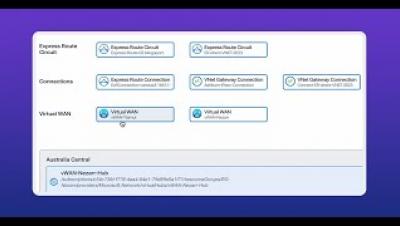
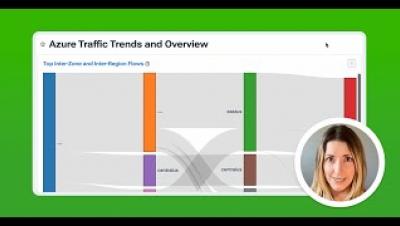
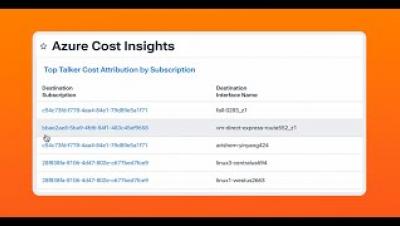
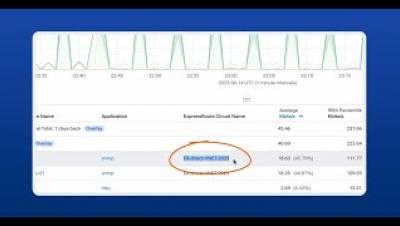
In this Kentik demo, Phil Gervasi shows how to perform a forensic analysis after a security breach. Leveraging Kentik's robust visibility into public cloud traffic, we showcase how engineers can effectively identify, analyze, and respond to security incidents. Through a hypothetical scenario, we trace a security alert from its origin—a suspected attack on an Azure-hosted system—to its resolution. Using tools like the Kentik Map and Data Explorer, we identify the attacker's entry point, compromised internal devices, and potential data exfiltration activities.