- February 2025 (1)
- January 2025 (2)
- December 2024 (2)
- November 2024 (3)
- October 2024 (4)
- September 2024 (3)
- August 2024 (2)
- July 2024 (4)
- June 2024 (2)
- May 2024 (5)
- April 2024 (7)
- March 2024 (7)
- February 2024 (8)
- January 2024 (5)
- December 2023 (1)
- November 2023 (3)
- October 2023 (4)
- September 2023 (3)
- August 2023 (4)
- July 2023 (3)
- June 2023 (2)
- May 2023 (2)
- April 2023 (3)
- March 2023 (1)
- February 2023 (5)
- January 2023 (4)
- December 2022 (3)
- November 2022 (4)
- October 2022 (2)
- September 2022 (4)
- August 2022 (3)
- July 2022 (2)
- June 2022 (1)
- May 2022 (1)
- April 2022 (4)
- March 2022 (4)
- February 2022 (1)
- December 2021 (2)
- November 2021 (1)
- September 2021 (2)
- August 2021 (2)
- July 2021 (1)
- June 2021 (4)
- May 2021 (8)
- March 2021 (3)
- February 2021 (3)
- December 2020 (4)
- November 2020 (4)
- October 2020 (5)
- September 2020 (3)
- August 2020 (3)
- July 2020 (3)
- June 2020 (4)
- May 2020 (2)
- April 2020 (5)
- December 2019 (1)
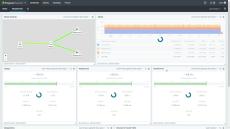
The Flowmon solution creates a secure and transparent digital environment where people rule the network regardless of its complexity and nature. Using machine learning, heuristics and advanced analytics, it enables IT professionals to improve performance and reduce risk across on-premise, datacenter and cloud environments. The solution serves as a shared platform where network and security teams speak the same language, enabling them to work as one for faster mean-time-to-resolve and optimal resource allocation. By delivering highly streamlined deployment to any network type, market-leading support and in-product guidance, the solution provides the fastest time-to-value in the industry.
Unified Digital Performance and Security Solution for:
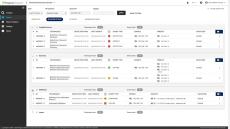
- NetFlow/IPFIX Monitoring: The Flowmon appliance captures, stores and processes network telemetry data, including normalization, visualization and analysis.
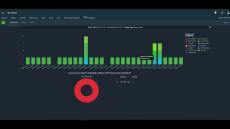
- Network detection and response to cyber threats: Flowmon detect suspicious behaviours, insider threats, unknown threats and other risks that bypass traditional approaches
- Network Performance Monitoring and Diagnostics across on-premise, cloud and hybrid environments.
- End-User Experience Monitoring: SaaS, cloud or on-premise, monitor critical app performance unobtrusively and at zero cost in resources. Let applications work for you.
- Infrastructure Design & Deployment: Understanding traffic structure is how you fine-tune your network configuration.
- Incident Monitoring & Investigation: Get a clear understanding of relevant events and their circumstances.
- Encrypted Traffic Analysis: No decryption. Get your complete analytics in real-time without losing privacy.