Operations | Monitoring | ITSM | DevOps | Cloud
April 2022
Network Monitoring Safety Checklist-5 Steps to Take
Network monitoring is a vital part of your security architecture and layered security portfolio. Step one in your network monitoring safety checklist is making sure you have network monitoring in the first place. The rest of our steps assume you have network monitoring and lay out five ways to optimize its value.
How Network Monitoring Defuses Hacker Bombs
You know by now that hackers literally never sleep. Chances are your network has been hit before and absolutely will be hit again. Hackers invent new techniques every day and tweak existing ones, many of which are automated—which is why we can say that hackers literally never sleep. Hackers either attack your network directly or attack your infrastructure through your network. Either way, the network itself is your first line of defense.
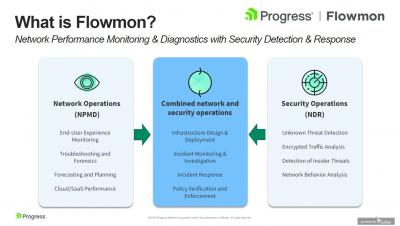
Advanced Traffic & Security Analysis in WhatsUp Gold with Progress Flowmon
Network Alerts-Monitoring and Notifications
When it comes to IT, you can’t do anything with an asset you can’t see. When it comes to your networking, monitoring offers the eyeballs to know what is going on. But IT and network pros don’t spend all day staring at a dashboard waiting for something to happen. Like your local police department, they rely on notifications of trouble. Instead of 911 calls, IT depends on network alerts.