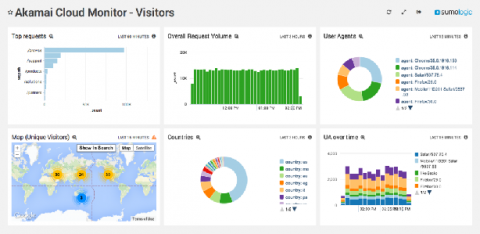
How to Monitor Akamai Logs
Some of the largest and most prominent websites, worldwide, partner with Akamai to provide their customers with a premium web experience. What benefits could Akamai offer to you and your online product offerings? In this article, we will introduce you to Akamai and the services they provide. We’ll talk about why those services are essential and how they can help you provide a better online experience for your customers. We’ll also talk about how Akamai can protect you from cyberattacks.