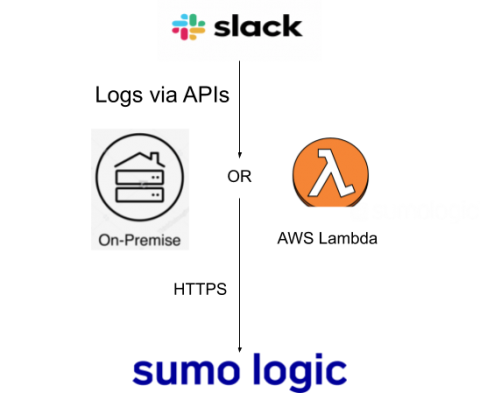
How to Collect Kubernetes Data
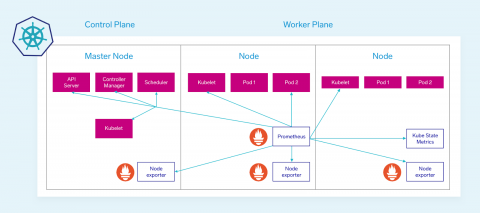
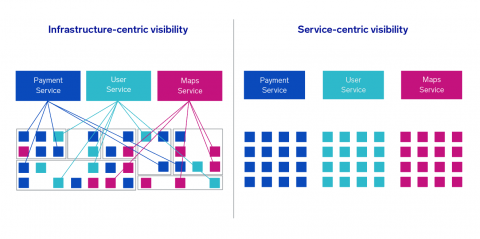
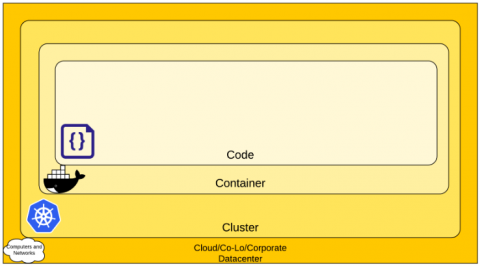
Now that we understand what machine data is available to us, how do we get to this data? The good news is that Kubernetes makes most of this data readily available, you just need the right tool to gather and view it. The solution we will discuss here heavily utilizes open source tools for collection and data enrichment because of their deep integrations and overwhelming community support.