A Healthy Outlook on Security From RSA Conference 2020
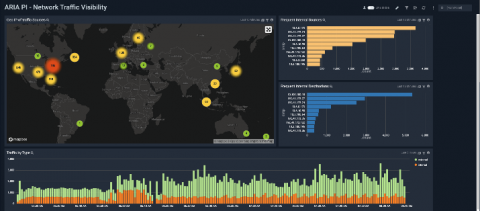
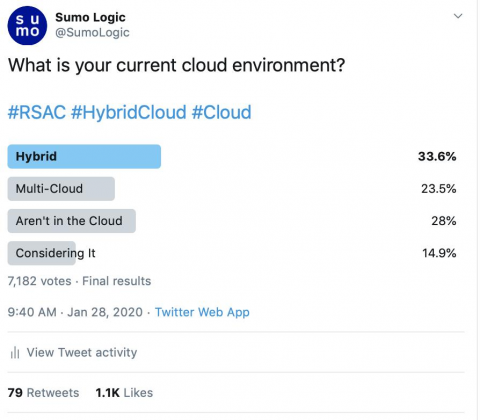
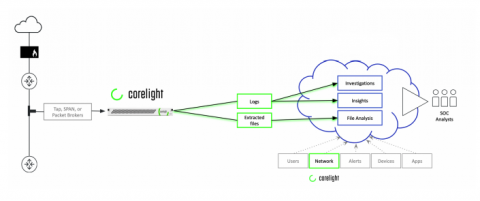
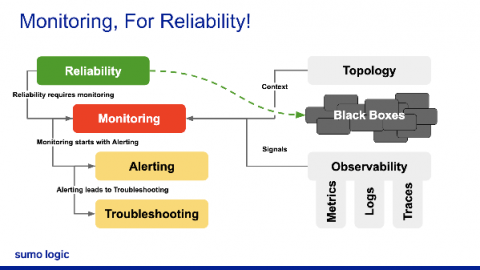
Another RSA Conference is in the books and despite a few vendors pulling out due to public health concerns, the show went on and offered attendees a glimpse of what lies ahead in the world of cybersecurity. The main theme for this year’s RSA event focused on the human element in addressing the behaviors and activities of users and analysts.