How Big Data and Log management work hand in hand
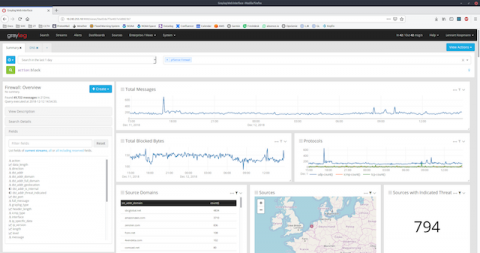
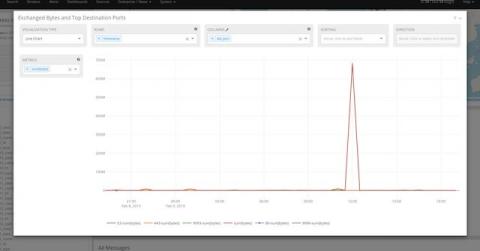
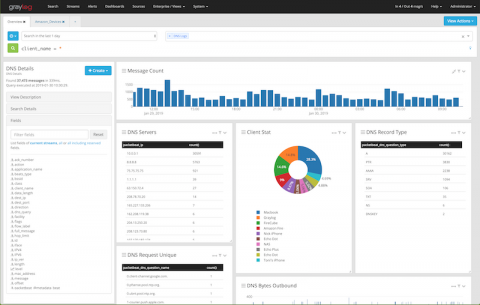
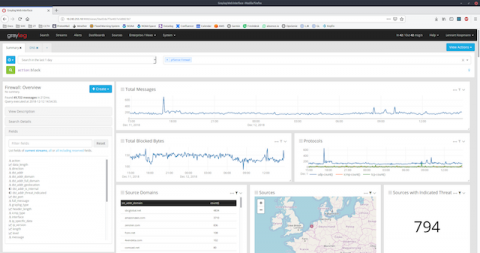
As Stephen Marsland once said, “if data had mass, the earth would be a black hole.” A vast part of the immense amount of structured and unstructured data that we call “Big Data” is nothing but machine-originated log data. Logs are generated for a lot of different purposes – from security to debugging and troubleshooting. They constitute a gold mine of useful information and actionable insights if properly stored, managed, and analyzed.