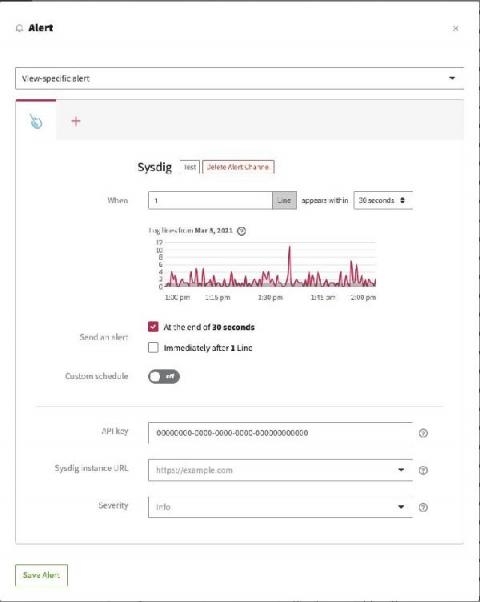
Detecting and Mitigating CVE-2021-25737: EndpointSlice validation enables host network hijack
The CVE-2021-25737 low-level vulnerability has been found in Kubernetes kube-apiserver where an authorized user could redirect pod traffic to private networks on a Node. The kube-apiserver affected are: By exploiting the vulnerability, adversaries could be able to redirect pod traffic even though Kubernetes already prevents creation of Endpoint IPs in the localhost or link-local range.