The Complete Guide to Log Parsing
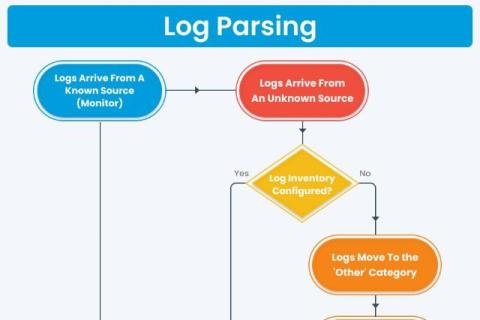
One of the most important steps in log management is parsing of the log files, which turns unstructured data into understandable information. Logs are broken down by pre-established parsing rules, making monitoring and operating system performance easier and facilitating real-time problem-solving of the event logs. A Data Breach Investigations Report emphasizes the critical role of human error in cybersecurity, noting that it is a factor in 74% of all breaches.