Troubleshooting Kubernetes Deployment at Every Level!
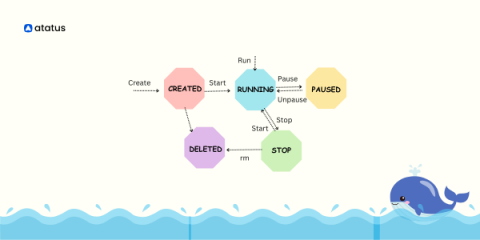
Kubernetes has emerged as the de facto standard for container orchestration, with its ability to automate deployment, scaling, and management of containerized applications. However, even with the best practices and expertise, Kubernetes deployment can sometimes be a complex and challenging process. It involves multiple layers of infrastructure, including the application, Kubernetes cluster, nodes, network, and storage, and each layer can have its own set of issues and challenges.