Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
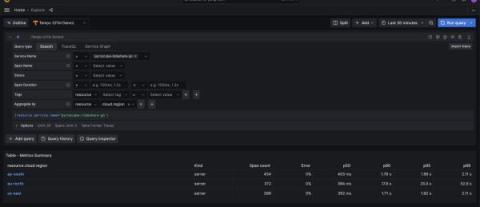
Traces to metrics: Ad hoc RED metrics in Grafana Tempo with 'Aggregate by'
In observability, finding the root cause of a problem is sometimes likened to finding a needle in a haystack. Considering that the problem might be visible in only a tiny fraction of millions or billions of individual traces, the task of reviewing enough traces to find the right one is daunting and often ends in failure.
Learning by Example with Cribl's New Lookup Examples Pack
In the world of data management, Cribl offers various methods to enhance data using the Lookup Function and many C.Lookup Expressions. While Cribl’s documentation is comprehensive, practical examples are often the most effective learning tools. That’s why we’ve introduced the new Lookup Examples Pack.
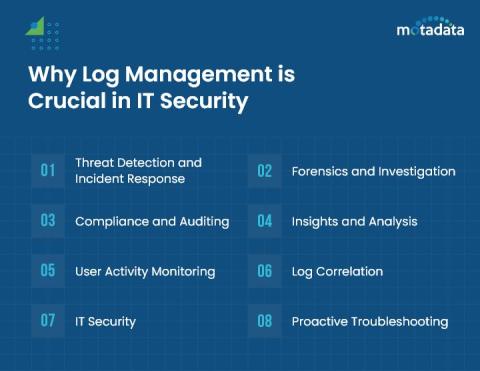
Importance of Log Management in IT Security
Around 70% of companies experienced cyberattacks in the past year. With this increase in cyberattacks, the importance of log management in IT security has also increased over the years. That’s the reason why small and enterprise businesses have started to invest in log management tools to protect their businesses from cybersecurity breaches.