Combining Log Analysis with Continuous Delivery to Reduce Release Cycle Times
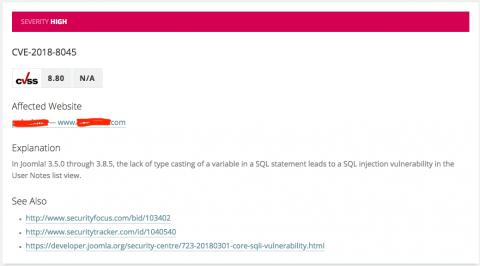
One of the biggest challenges in the field of log analysis is being able to connect the dots and understand the underlying story connecting them. Applications and machines are generating an increasing amount of log data, making it extremely difficult to separate the wheat from the chaff.