Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Preventing and mitigating data loss with Graylog
If you’re handling sensitive information, dealing with data loss can be more than just a headache. Log management tools such as Graylog can enhance your incident response and management strategies, and help you mitigate the damage when a breach occurs in your database. Minimizing data loss with a fast and scalable logging solution is key if you want to bring your cybersecurity to the next level.
What Is MTTF? Mean Time to Failure Explained in Detail
“What is MTTF?” That’s the question we’ll answer with today’s post. Yep, the article’s title makes it evident that the acronym stands for “mean time to failure.” But that, on its own, doesn’t say anything. What does “mean time to failure” actually mean? Why should you care? That’s what today’s post covers in detail.
[KubeCon Recap] How to Debug Live Applications in Kubernetes
Joe Elliott, a backend engineer at Grafana Labs, took the stage in front of a packed house at KubeCon + CloudNativeCon in San Diego to demonstrate a few of the tricks he uses to debug applications live in Kubernetes. The goal is to increase your knowledge of applications in the production environment. Elliott’s techniques are framework agnostic and Linux-specific, and they are most useful in situations where you have a known type of problem and application.
Why businesses need to suit up against cyberattacks in 2020
Cyberattacks are never going away; in fact, things appear to be getting worse. The complexity of attacks has escalated, resulting in more sophisticated, targeted takedowns. Just look at the attacks in Baltimore, Atlanta, Florida, and Spain within the past few years. Organizations around the world have had their operations halted by ransomware, with some taking weeks to get back to normal.
Inline Image Scanning for AWS CodePipeline and AWS CodeBuild
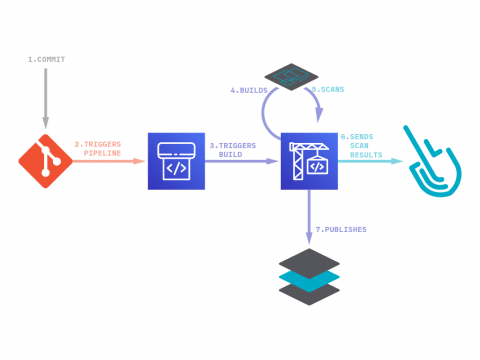
In this blog post you’ll learn how to set up image vulnerability scanning for AWS CodePipeline and AWS CodeBuild using Sysdig Secure DevOps Platform. AWS provides several tools for DevOps teams: CodeCommit for version control, CodeBuild for building and testing code, and CodeDeploy for automatic code deployment. The block on top of all these tools is CodePipeline that allows them to visualize and automate these different stages.
AWS ECR Scanning with Sysdig Secure
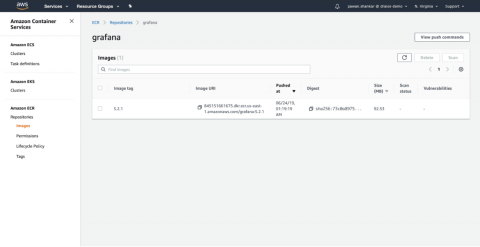
As container adoption in AWS takes off, ECR scanning is the first step towards delivering continuous security and compliance. You need to ensure you are scanning your images pulled from AWS ECR for both vulnerabilities and misconfigurations so that you don’t push applications running on AWS that are exploitable.
Sysdig extends security across all AWS container services
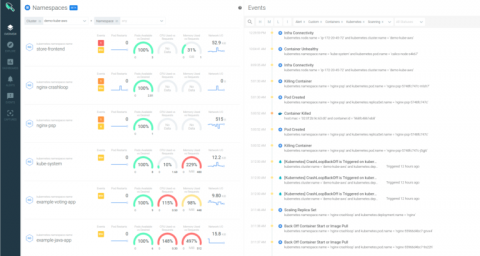
Cloud teams are increasingly adopting AWS container services to deliver applications faster at scale. Along with the roll out of cloud native architectures with containers and orchestration, what’s needed to stay on top of the security, performance and health of applications and infrastructure has shifted. At Sysdig, we’ve worked with Amazon to provide tools and integrations that help secure your Cloud Native workloads deployed across all AWS container services.
How AIOps Can Help Deliver Key ITOM Insights
Building an agile team's 'safety harness' with cmocka and FOSS
Netdata is made up from agile teams who are deeply committed to improving the usability of our product. We want to respond to our users and introduce in-demand features. Working directly with our community is the best way to make Netdata better. But we face the same the dilemma as all agile teams: How do we do this safely?