How to Automate the Handling of Suspicious User Behavior
We live in a technological society, and cyber attacks are on the rise. Much of this fraudulent behavior is linked to malicious actors or gangs of cyber criminals who are trying to exploit anything they can get their hands on. By using tools like Cobalt Strike or customized alternatives, they attempt to penetrate an organization’s defenses in order to gain leverage, exfiltrate PIIs, plant ransomware or CnC beacons, or perform other kinds of malicious acts.
Unfortunately, identifying fraudulent behavior can be quite difficult. It mainly depends on the organization’s policies for fair use of services and activities. In addition, manually configuring security policies and business workflows in order to detect and correct anomalous behavior is not scalable in the long run. You will need a better plan to tackle these issues efficiently and effectively.
In this article, we will explain the nature of suspicious user behavior, why it’s an issue, and why it’s critical to automate the handling of suspicious user behavior as part of your organization’s security strategy.
What Is Suspicious User Behavior?
As the name implies, suspicious user behavior is a set of actions taken by a user (who may or may not be authenticated) that are deemed suspicious or geared toward circumventing your existing security controls. You should define which actions should be labeled suspicious beforehand on a case-by-case basis. For example, if you are operating a video streaming service and you have explicitly forbidden access to users outside of a particular geographic area due to licensing reasons, then you should consider putting VPN and geo restrictions in place. You need to be able to capture the client traffic and detect if it is coming from IP ranges outside of the allowed coverage area.
Another example of suspicious user behavior is when a user performs actions from different locations during a window of time when it would be impossible to travel between them. This is called “impossible travel action.” If you also see suspicious IP addresses or access from locations where a particular user has never been before, then you can assume that something might be wrong.
Having a predefined set of policies and classifiers that match your organization’s requirements is the first crucial step in defending your business. The second step is to work toward automating the whole process of detecting and remediating malicious user behavior. Below, we will explain why this is necessary.
The Benefits of Automating the Handling of Suspicious User Behavior
Automating the process of handling suspicious user behavior provides many measurable benefits. The most important one is saving time. You cannot sustain a business when your staff is working 24/7 on manual tasks to detect and remediate the continuous threat of fraudulent activities performed by malicious actors or bots. Instead, you need to use this time to improve and fine-tune your policy rules and workflows, gather data, and perform analyses that are crucial for the accurate and timely handling of fraud.
Saving this time gives your security teams a chance to perform simulations or incident response drills. If a bad actor penetrates your defenses, you’ll be able to bounce back quickly with remediation measures as well as postmortems that will improve your workflow and minimize the risk that the security breach will recur. All of the time that you spend fortifying your defenses against abnormal user behavior will also complement your efforts to battle anomalous behaviors for other types of activities.
Next, we will explain how to automate this process.
How to Automate the Handling of Suspicious User Behavior
Now that you’ve got a basic understanding of what suspicious user behavior is and why you need to automate the steps to handle it, let’s take a look at some practical ways to do just that. As an example, let’s say that you’ve noticed the following user behavior:
- A user logged in from a new device.
- The system compared it to the list of known user devices and flagged this deviation. It then sent a MFA prompt to the client.
- The user failed MFA.
- The user tried to log in again and failed several more times.
- The user then tried to log in from several different devices and IPs.
- The user tried to enter passwords from a rainbow table that should not be allowed in the first place.
- The user submitted a ticket on your platform to try to gain access, but failed to provide sufficient identification or the answers to basic security questions.
With this series of steps in mind, how would you design and implement a system that could trigger automated rules and suspend user accounts after a specific number of failed attempts? How would you prevent the suspension of the account if the system recognized the user as legitimate? How would you set it up so that you could add new rules or amend policies on demand?
This would be all but impossible to do using traditional code, since there are many conditionals in this situation. What you need is a visual workflow engine that is easy to configure and customize to enforce rules and policy decisions. For example, you want a high-level diagram like this:
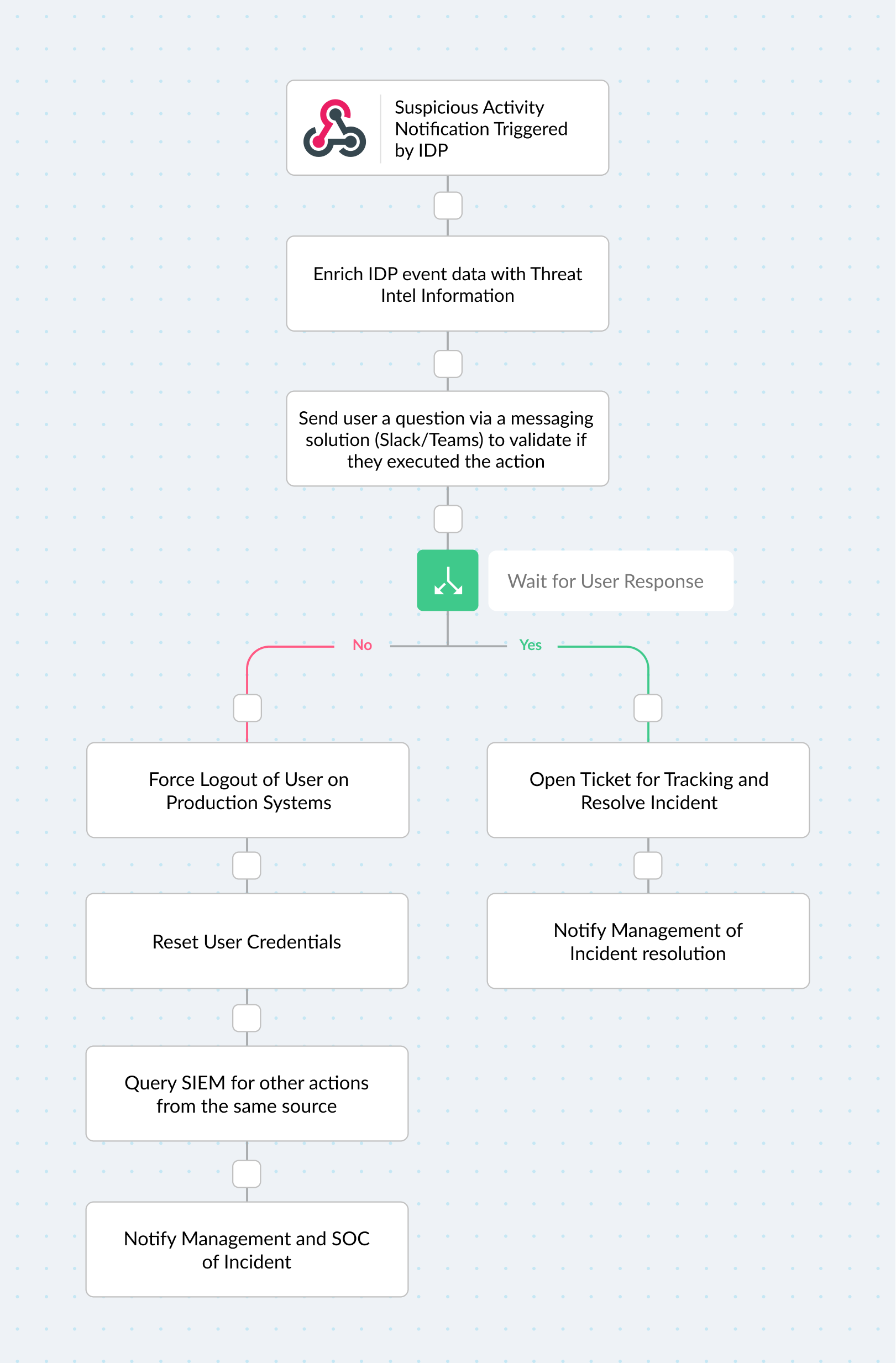
Example of an automated workflow to manage suspicious user behavior
The best way to meet these requirements is to leverage easy-to-use, low-maintenance software. You establish normal behavior and log collection (IPs, device info, and requests), then funnel them into a workflow that makes decisions based on a template that your security team defined beforehand. Once certain criteria are met, the system can make decisions about the nature of the user behavior.
If the behavior is deemed suspicious, the system can suspend the user, notify the user that the account was suspended, quarantine the user’s endpoint, and open a help desk ticket to restore the user account upon request. Otherwise, you can just thank the user for utilizing your platform.
By leveraging a straightforward, secure tool built for the purpose of defining and applying business logic to your workflow, you can achieve flexibility and conformity when defending your business from illegitimate user behavior.
Where to Start with Security Automation Software
If you are ready to level up your organization’s security posture and automate some of your security processes, look no further than Torq. Torq is the leading provider of no-code security automation software, and they solve the difficult problems of defining and applying organizational policies for you.
When it comes to automating your process for handling suspicious user behavior, Torq offers an intuitive policy workflow builder that comes packed full of excellent features such as user behavior validation, verification of notable or suspicious sources, and detailed auditing.
You can schedule a free demo to see how they can help you set up your workflows with no coding or professional services required.

