Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Kubernetes Q3-2020: Threats, Exploits and TTPs
Kubernetes has become the world’s most popular container orchestration system and is taking the enterprise ecosystem by storm. At this disruptive moment it’s useful to look back and review the security threats that have evolved in this dynamic landscape. Identifying these threats and exploits and being a proactive learner may save you a lot of time and effort…as well as help you retain your reputation in the long run.
What Is an MSP and What Makes It Unique in the IT World?
Email Security Risks: Why You Need a Cyber Security Plan
Even though technology has advanced significantly over the past few decades, hackers and cybercriminals still target large volumes of email messages daily. Some of the biggest types of things that get sent through email include malware, ransomware, trojans, and viruses. These things are often disguised in some sort of “friendly” email message, an embedded link, or a cute kitten meme.
System extensions are replacing macOS kernel extensions. How will this affect you?
From the outset, Apple has been keen to protect user privacy and security, and deprecating kernel extensions is one of the company’s latest moves towards modernizing its platform. As part of Apple’s sustained effort to make macOS a more reliable and secure platform, the tech giant announced at WWDC 2019 that kernel extensions are going to be replaced in macOS Catalina with Apple’s new technology, system extensions. But, why should you care? Let’s explore now.
Monitor SSL TLS Certificate Expiration
Secure Socket Layer (SSL) and its successor, Transport Layer Security (TLS) are protocols designed to safeguard traffic over the internet. SSL certificates allow websites to move from HTTP to HTTPS, a more secure communication channel on a network. Starting this September, the lifespan of an SSL/TLS certificate will be limited to 398 days, a reduction from the previous maximum certificate lifetime of 825 days.
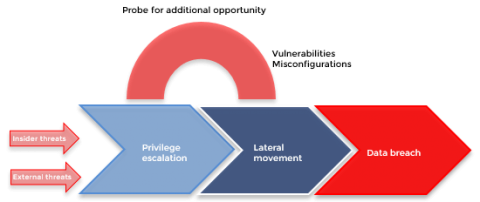
Advanced Active Directory attacks: Simulating domain controller behavior
There was a time when cyberattacks on identity and authentication infrastructures [like Active Directory (AD)] were immensely challenging to perform. A lot of forethought had to be put into devising a plan for the careful execution of attacks, and advanced technical knowledge of domains and networks was a requisite. Over time, with the advent of open-source pen testing tools, the knowledge gap and the complexities involved to carry out a full-scale cyberattack have narrowed drastically.
Sysdig Boosts AWS Security with the First Automated Inline Scanning for Fargate
Automate Fargate image scanning
Discover how to automate AWS Fargate image scanning directly in your AWS environment and block vulnerabilities from reaching production, among other threats. AWS Fargate and ECS allow you to deploy containerized workloads quickly. Fargate is even more convenient, as you don’t have to take care of the infrastructure.
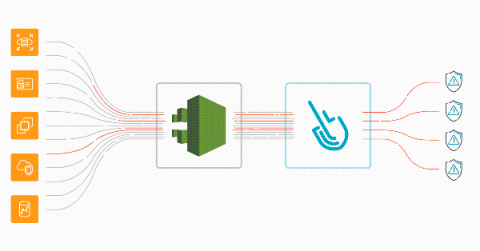
AWS threat detection using CloudTrail and Sysdig Secure
Implementing AWS threat detection with Sysdig Secure takes just a few minutes. Discover how to improve the security of your cloud infrastructure using AWS CloudTrail and Sysdig Cloud Connector. With the rise of microservices and DevOps practices, a new level of dangerous actors threatens the cloud environment that governs all of your infrastructure. A malicious or inattentive cloud API request could have a sizable impact on availability, performance, and last but not least, billing.