Operations | Monitoring | ITSM | DevOps | Cloud
%term
Announcing Stackdriver Kubernetes Monitoring: comprehensive Kubernetes observability
Icinga Monthly Snap April: Berlin Meetup, Releases and Themes
April brought us new bugfix releases of Icinga 2 v2.8 and Icinga Web v2.5. Carsten released new versions for the Grafana module for Icinga Web 2.
Instrument Your Rails Apps Automatically With Honeycomb's New Rails Integration
You’ve always been able to get observability for your Ruby apps by instrumenting them with our SDK, affectionately known as libhoney. Unfortunately, instrumenting code you’ve already written is nobody’s favourite job. If only there were some way to automate the repetitive parts, so you could get instant insight into what your app is doing in production, and then focus your effort on augmenting that insight with the information that’s unique to your app!
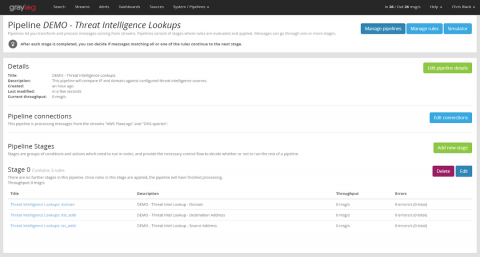
Integrating Threat Intelligence with Graylog
In my last post, I gave a high-level overview how to select a threat intelligence vendor and how to integrate indicators of compromise (IOCs) into your SIEM or log management environment. In this post, I will describe in detail how to use the Threat Intelligence plugin that ships with Graylog. I’ll start with the steps necessary to prepare your data, then explain how to activate the feature and how to configure it for use.
Be GDPR Ready: Prepare Your Log Data
Organizations both small and large that deal with personal data must be compliant with GDPR rules. At Coralogix, we’ve been working hard to be prepared for GDPR. Preparing your data for GDPR can be a daunting task, so we thought we’d shed some light on the issue.
So What is Observability Anyway
It’s amazing. It’s brand new. Everyone needs it. It is “the next best thing”. Only half of these statements are true, it is not new and it is not the next best thing. It is branding an existing paradigm that many companies use and rely on—but—it is amazing and everyone should want it. If you’re new to the concept, what does observability really mean and how can it help transform your operations?
Monitoring Websites – Create Web Trackers
Have any of your website or web applications gone down, been hacked, or defaced? When and how did you find out? In this post, we will show you how Netmon monitors your websites (or web applications) in our complete Network Monitoring Solution.
First quarter 2018 results
We have started strong! We’ve crossed the finish line for the first quarter, and our revenue gains beat out first quarter 2017 by 26%!
GDPR: Top 5 Logging Best Practices
The rather broad definition of personal data in the GDPR requires paying special attention to log data. GDPR and personal data in web server logs is a popular topic in many GDPR fora. For example, IP addresses or cookies might be considered personal data. Consequently, such data must be stored only with the consent of customers for a limited time. It is highly recommended to anonymize personal data before you hand over the logs to any 3rd party to minimize risk.