The Importance of Log Management and Cybersecurity
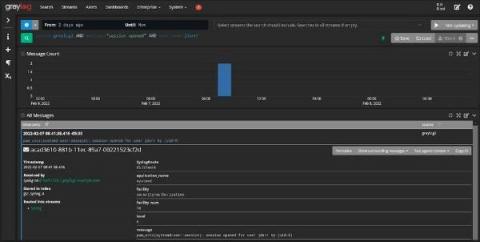
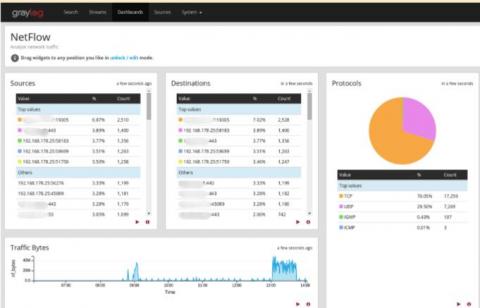
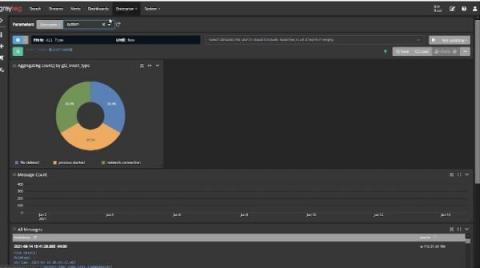
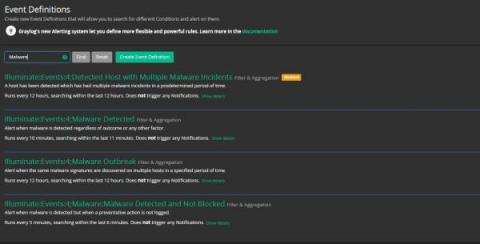
Struggling with the evolving cybersecurity threat landscape often means feeling one step behind cybercriminals. Interconnected cloud ecosystems expand your digital footprint, increasing the attack surface. More users, data, and devices connected to your networks mean more monitoring for cyber attacks. Detecting suspicious activity before or during the forensic investigation is how centralized log management supports cybersecurity.