Navigating the Future of Exposure Management
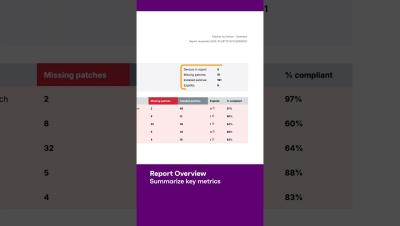
Navigating the Future of Exposure Management The future of exposure management involves overcoming integration challenges within organizations. Analysts call for a shift towards platformization and a risk-based approach, emphasizing asset discovery and visibility. No single vendor can fulfill all needs, highlighting the importance of a multi-vendor ecosystem. Various vulnerability scanners, including traditional and cloud types, are essential. Effective remediation requires prioritization, workflow integration, and teamwork to address vulnerabilities and updates.