Operations | Monitoring | ITSM | DevOps | Cloud
February 2019
Browser vulnerabilities: Securing against the inevitable
Web browsers have revolutionized the way we use the internet. They’ve escalated employee productivity, but have also opened up organizations to a plethora of security loopholes. Browsers are the easiest point of entry for hackers to exploit a system because they contain vulnerable components like plug-ins and cookies.
Applications Manager recognized as 2019 Gartner Peer Insights Customers' Choice
The new year has begun on a grand note for us, and we couldn’t be happier! We’re thrilled to announce that ManageEngine’s Applications Manager has been named 2019 Gartner Peer Insights Customers’ Choice for application performance monitoring (APM) suites. We take great pride in this distinction, as it’s solely based on your feedback, and it’s your feedback that pushes us to new heights.
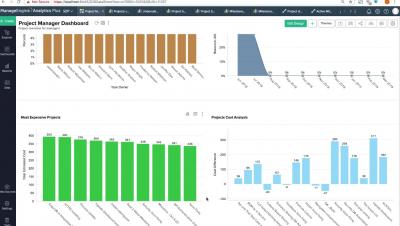
Analytics Plus webinar: How to manage IT projects like a pro using analytics
Five worthy reads: The business benefits of serverless computing
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore serverless computing and how it can impact business operations.
Seven reasons your help desk needs analytics.
Help us understand and measure your SOC performance [Survey]
What gets measured gets managed. You probably intuitively sense the truth in that statement, but are you practicing it? Specifically, are you measuring your security operations center’s (SOC) performance? Measuring the IT security team’s performance has always been subjective. With more and more security techniques emerging in the last decade, your organization may have come up with different metrics to measure the performance of its SOC.
Five worthy reads: AI and ML: Keys to the next layer of endpoint protection
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we’ll talk about why incorporating AI into your UEM strategy may be inevitable.
IT analytics in 90 seconds: Spot areas that hamper technician performance
Tracking insider threats with AI
If you thought masked hackers in dark rooms spreading malware were your only security concern, think again. In its Insider Threat Report for 2018, Crowd Research Partners brought to light that almost 90 percent of organizations find themselves vulnerable to insider threats. What’s worse is that 50 percent of these organizations experienced an insider attack in 2018.
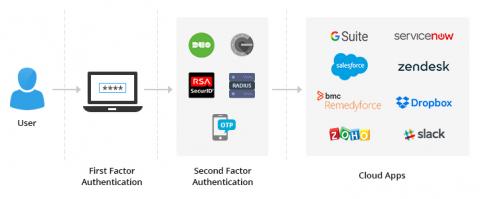
Thwart password spray attacks to secure employee access to cloud apps
Chances are you’ve heard of traditional credential-based attacks on Active Directory (AD) and cloud applications—brute force attacks, dictionary attacks, and keylogging, to name a few. There’s now another attack type you should familiarize yourself with: password spray attacks. In this blog, we’ll analyze why you should be wary of them and the best way to tackle them.
IT analytics in 90 seconds: Crack down on long-pending requests in your help desk
Five worthy reads: Augmented analytics paves the way
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we look at the rise of augmented analytics and how it tackles the ever growing need for intelligent, data-driven insights.