Operations | Monitoring | ITSM | DevOps | Cloud
Insider Threats
6 Signs Your Company is Experiencing Data Breaches
Monitor User Behavior to Detect Insider Threats
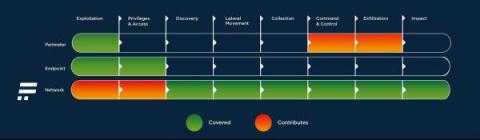
The risk from insider threats has grown massively, with perpetrators frequently getting around organizations' increasingly complex perimeter protections. It is one of the most common ways customer data or industrial and trade secrets leak. This very complex topic includes many types of threats and techniques. Let's discuss how you could detect insider threat activity at a network level.
Building a Multi-Tenant Insurance Platform
What Is Phishing? Insider Risk & How to Prevent It
Insider Risk: The Call is Coming from Inside the House
Security-Rich: How the D2iQ Kubernetes Platform Meets NSA/CISA Kubernetes Security Hardening Guidelines
Cybersecurity continues to be a thorny problem for businesses and government agencies as breaches, disruptions, and data thefts continue to escalate. To help ensure that the growing number of government and private organizations implementing Kubernetes solutions have the highest possible levels of security, the National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) have issued guidelines for hardening the security of Kubernetes implementations.
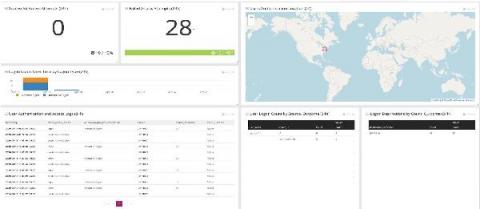
Monitoring Logs for Insider Threats During Turbulent Times
For logs and tracking insider threats, you need to start with the relevant data. In these turbulent times, IT teams leverage centralized log management solutions for making decisions. As the challenges change, the way you’re monitoring logs for insider threats needs to change too. Furloughs, workforce reductions, and business practice changes as part of the COVID stay-at-home mandates impacted IT teams.
What's New with Ivanti Device and Application Control 5.3
What’s New in Ivanti Device & Application Control 5.3 Nearly every company in the world incorporates a Mac endpoint into the organization. Without a device control solution to manage these stations we see a real possibility for data leakage risk. This loss happens mainly because of insider threats. Ivanti Device and Application Control has historically performed well protecting our customers against these types of threats, but the Mac endpoints can still represent a risk.
Measures to be Taken Against Insider Threats
Insider threats are becoming a growing concern across different industries. Most coverage goes to outside attacks, especially when it comes to big corporations and government agencies. However, internal security is something organizations need to take very seriously to avoid irreparable damages. Not many enterprises can afford internal threat detection programs. However, they can definitely adopt proactive measures to avoid them, especially when it comes to sensitive systems and data.