Operations | Monitoring | ITSM | DevOps | Cloud
Insider Threats
The Employee Offboarding Checklist for IT Pros
Tech Talk 3 Monitoring for Insider Threats
Our award-winning IAM and insider threat prevention solutions highlighted at RSA Conference 2020
ManageEngine brought home its first set of accolades for 2020: two InfoSec Awards presented by Cyber Defense Magazine at RSA Conference 2020. Amidst the over 3,000 cyberdefense innovators that were assessed by Cyber Defense Magazine for its 2020 InfoSec Awards, ManageEngine was recognized for its identity and access management (IAM) offering, AD360, and for its insider threat prevention in Log360.
Prevent Data Breaches & Insider Threats
Prevent Data Breaches & Insider Threats
Find out which of your employees pose the greatest security risk
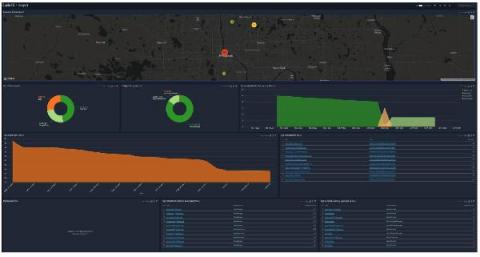
Among the different types of cyberattacks, insider threats are the hardest to track and have the highest rate of success. This can be attributed to their use, or rather misuse, of legitimate credentials, machines, and access privileges. Traditional SIEM solutions use simple rule-based alerting to detect potential insider threats, which cannot analyze user behavior or detect any anomalies therein.
Five Tools for User Activity Monitoring
As discussed in our blog post [What is User Activity Monitoring?], user activity monitoring (UAM) is a form of surveillance that provides visibility and insight into employee productivity and engagement while also revealing insider security threats. While UAM on company-owned or company-sanctioned devices and networks is legal, ethical and HR considerations require that UAM be implemented with a high level of professionalism and sensitivity.
What Is User Activity Monitoring?
User Activity Monitoring (UAM) tracks the behavior of internal end-users—employees, subcontractors, partners, and so on—on a company’s networks, devices, and other IT resources. UAM, sometimes also called employee monitoring, may be deployed for a number of reasons, such as providing insight into the productivity of both individual employees and the company as a whole. Is Employee X spending too much time browsing the internet for non-business purposes during work time?
Tracking insider threats with AI
If you thought masked hackers in dark rooms spreading malware were your only security concern, think again. In its Insider Threat Report for 2018, Crowd Research Partners brought to light that almost 90 percent of organizations find themselves vulnerable to insider threats. What’s worse is that 50 percent of these organizations experienced an insider attack in 2018.