Audit Trails Are Critical for Tracking Network Activity
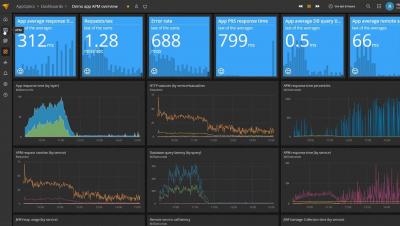
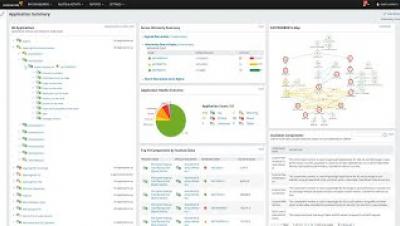
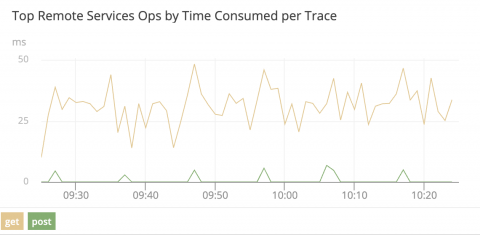
As networks become more distributed and complex, it’s becoming ever more challenging for IT professionals to track all the events happening on their networks. Still, it’s vitally important to do so—logging activity on an agency’s network is critical to determining who’s on the network, what applications they’re using, and whether those applications can compromise the network and user data.