Operations | Monitoring | ITSM | DevOps | Cloud
Cyberattacks
Protecting Your VoIP Infrastructure From DDoS Attacks
Distributed denial of service (DDoS) attacks are an ongoing issue for communications service providers, putting critical systems at risk, undercutting service level agreements, and bringing unwanted headlines. In the first half of 2022 6 million of these attacks were reported. Some metrics of DDoS attacks in 1H2022 compared to 2H2021.
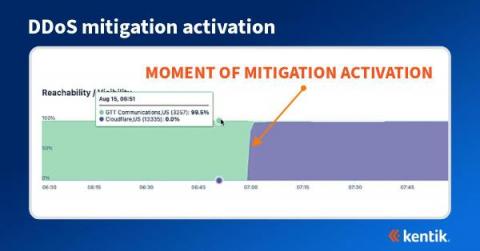
How BGP propagation affects DDoS mitigation
We often think of DDoS attacks as volumetric malicious traffic targeted against organizations that effectively take a service offline. Most frequently detected by anomalous behavior found in NetFlow, sFlow, IPFIX, and BGP data, what may not be well understood is how the DDoS mitigation works and how it’s possible to visualize the effectiveness of the mitigation during and after an attack.
How BGP propagation affects DDoS mitigation
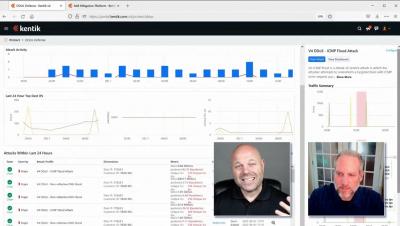
Detecting and Mitigating DDoS Attacks
3 Common Misconceptions about Executive Order 14028: Improving the Nation's Cybersecurity
The United States is the #1 target for cybersecurity attacks in the world. 38% of targeted cybersecurity attacks so far in 2022 were aimed at the United States data and systems. That’s alarming. And we see it in the news almost every day. Solarwinds, Colonial Pipeline, The Pulse Secure VPN zero-day… There’s an increasing number of threats and attacks, to the tune of 15.1% year over year.
Mind the Overspray - Password Spraying Remains a Major Threat
If you’re wondering if that classic car you’ve been scoping out on Bring a Trailer or eBay Motors is as authentic as posited by the seller – specifically re: the common claims of “original paint” or “high quality respray” – you’re going to want to take a closer look around the edges. This is because a talented painter can make a second or 30th-hand vehicle look pretty snazzy with a well-affected, if not super high-quality, repaint.
A NetOps Guide to DDoS Defense
Ransomware: Latest Variants and Trends on the Rise
Here in this blog, we will talk about some of the emerging ransomware you should know about and how you can prevent such attacks.
Debunking Myths About Cyberattack Complexity in 2022
Stoking fears about the threat landscape is a popular approach, and one that I don’t particularly care for. Many will tell you that the threat landscape is constantly changing, that threats are getting more complex, and that actors are getting more sophisticated. “The whole world is getting more difficult and scarier, so buy our stuff!” There’s a ton of media sensationalism too, with the popular image of the hacker sitting at a computer, wearing a dark hoodie.