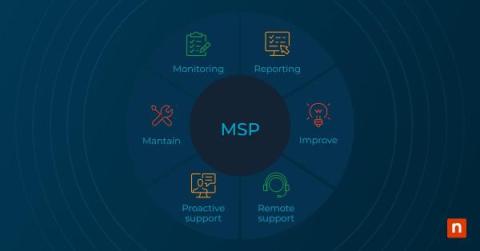
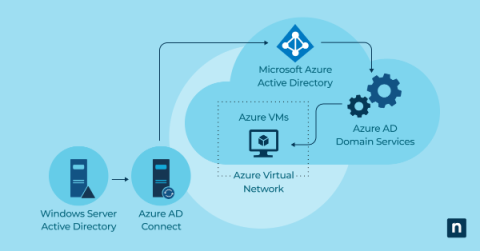
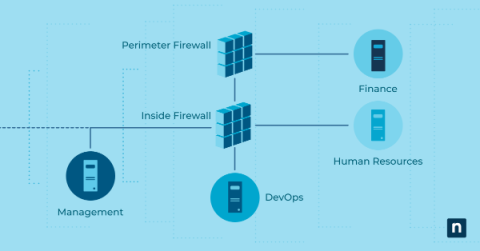
How to Choose a Managed Service Provider (MSP): 10 Factors to Consider
In today’s digitally driven world, businesses of all sizes rely heavily on technology to streamline operations, enhance productivity, and drive growth. However, managing complex IT infrastructure and staying ahead of rapidly evolving technologies can be a daunting task for organizations, especially those with limited resources and expertise.