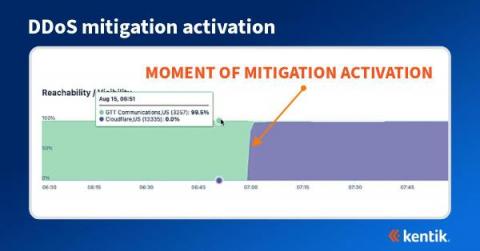
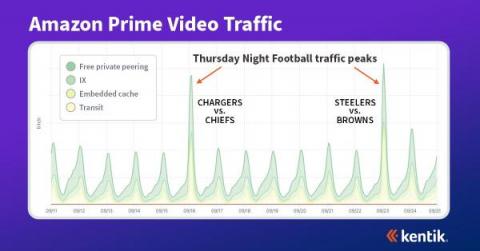
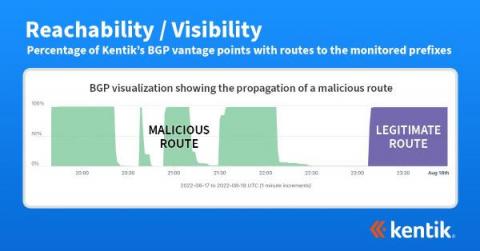
Are you a network observability champion?
At Kentik, we pride ourselves as innovators and thought-leaders for network observability. “Kentik is network observability” is more than a slogan for us. It’s an idea that informs our product roadmap and guides our problem-solving with customers. We’ve done a lot to explain network observability to prospects.