Kentik moves up the stack with Synthetic Transaction Monitoring
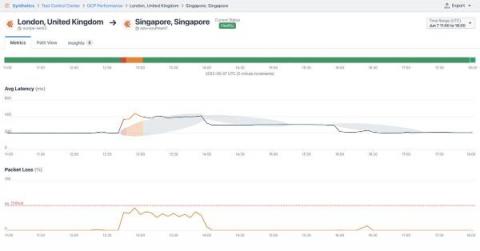
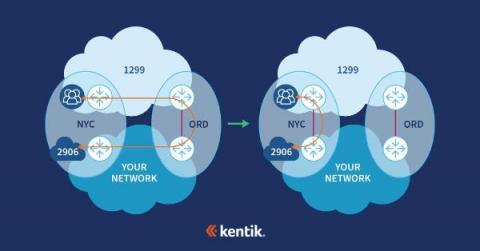
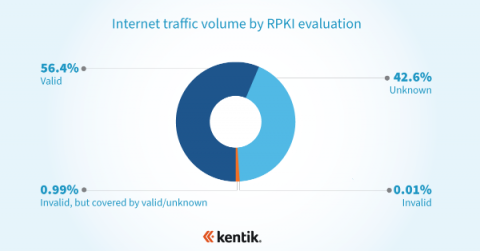
In our quest to provide the leading network observability solution, Kentik has been focused on developing a service for NetOps teams that empowers them to have intimate knowledge of their network traffic and the devices that route traffic. Our service helps them plan capacity, project costs, optimize routes, detect unwanted traffic, troubleshoot issues and analyze events.