Building trust in the digital realm: Safeguarding user experience amid website threats
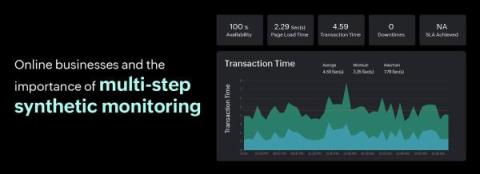
With an increasing number of organisations moving to online platforms and adding to the huge network of existing online sites, building and maintaining a trustworthy platform is of paramount importance for business. A secure platform not only safeguards sensitive information but also fosters confidence among users, paving the way for meaningful connections and lasting customer relationships.