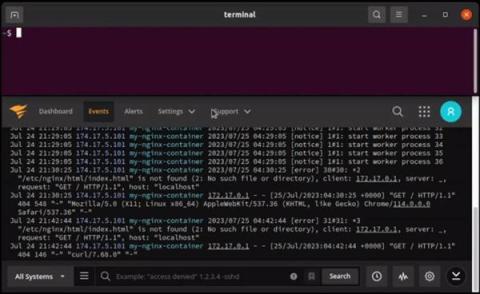
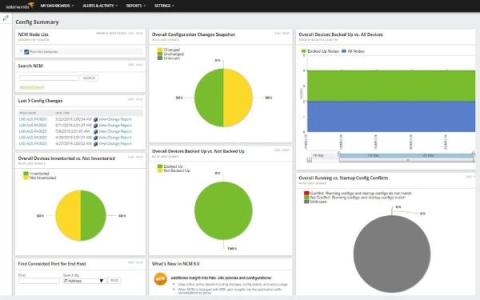
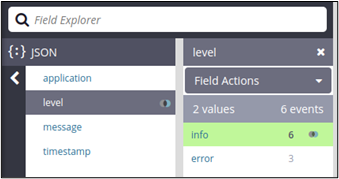
SQL Sentry Then and Now
With the release of SQL Sentry 2023.3, I look back at the past 18 years I have worked with the product to admire where it is today versus then. It’s been an incredible experience with a lot of moving parts, but no matter what market forces or acquisitions happen along the way, the core intention of “Improving the lives of Microsoft DBAs everywhere” has stayed the same. This is a two-part blog post: below, I’ll talk about our history and where we’ve come from.