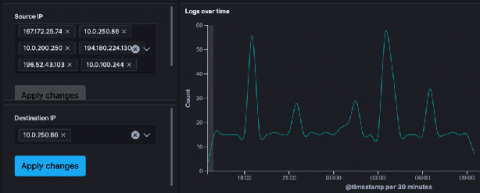
Investigate Stormshield & SonicWall Events with Logz.io Cloud SIEM
Stormshield and SonicWall are popular firewalls used to monitor network traffic for malicious actors. Firewalls can help detect all kinds of attacks, like brute force logins, DDoS, and SQL Injection, but they just make up a piece of the security puzzle. Most teams will have many other security tools that address different kinds of vulnerabilities and attacks.