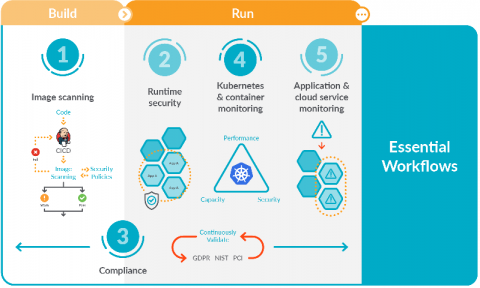
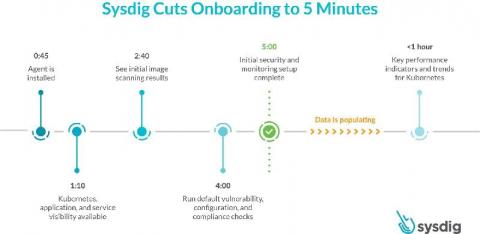
What's new in Kubernetes 1.19?
Kubernetes as a project is maturing, support has been increased from nine to 12 months, and there’s a new protocol in place to ensure a steady progress on feature development. Also, many of its new features are meant to improve the quality of life of its users, like Generic ephemeral inline volumes, or the structured logging.