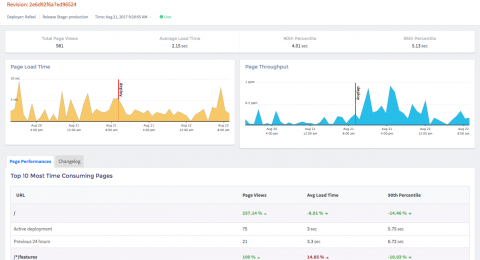
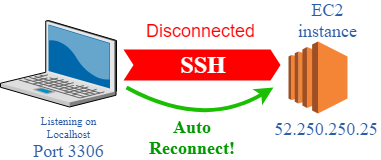
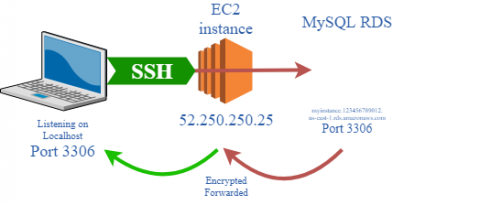
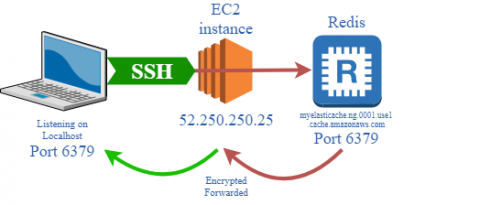
How to deploy infinitely scalable applications to AWS in minutes with Up & Semaphore CI
Many Apex Up users have been asking about integration with continuous integration platforms, this post walks through staging and deploying Up to production using Semaphore CI.