Operations | Monitoring | ITSM | DevOps | Cloud
Logging
The latest News and Information on Log Management, Log Analytics and related technologies.
Industry Cloud Platforms, Explained
Maturity Models for IT & Technology
Unpacking the Hype: Navigating the Complexities of Advanced Data Analytics in Cybersecurity
The cybersecurity industry is experiencing an explosion of innovative tools designed to tackle complex security challenges. However, the hype surrounding these tools has outpaced their actual capabilities, leading many teams to struggle with complexity and extracting value from their investment. In this conversation with Optiv‘s Randy Lariar, we explore the potential and dangers of bringing advanced data analytics and artificial intelligence tools to the cybersecurity space.
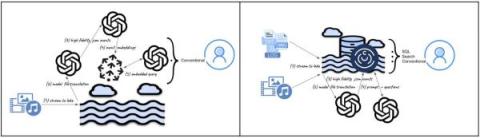
The Evolution of Search: How Multi-Modal LLMs Transcend Vector Databases
Getting to know Systems insights, a simplified database system monitoring tool
The story of how we simplified database system monitoring for generalists while making it flexible enough for specialists.
Field Data vs Doc Values | Understanding Elasticsearch Performance Issues
Introduction to Grafana Plugins
Grafana is a powerful open-source platform for monitoring and observability, but what truly makes it shine are its plugins. For technology engineers looking to expand Grafana's capabilities, plugins are the way to go. In this post, we'll dive into the world of Grafana plugins and offer some unique tips to get the most out of them.
Coralogix vs Grafana Cloud: Pricing, Features and More
While Grafana is one of the better known names in the industry, Coralogix offers a full-stack observability platform. Despite the popularity of the Grafana brand, the cloud based solution lacks in some key areas. This article will go over the differences between Coralogix and Grafana Cloud, from features, customer support, pricing and more.