Is Waiting for the Thaw Unbear-able?
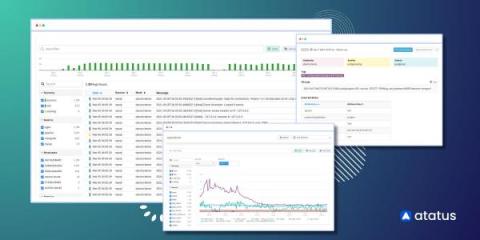
It’s not new news that organizations are producing more data than ever. But, in order to take advantage of this data, it needs to be collected, stored, retained, and then, at some point, analyzed. Most analysis tools also act as the retention point for this data. While this may (at first) appear to be the best option for performance, it quickly creates significant problems. First, those systems were never designed for the scale of today’s growing volume of data, currently at a 28% CAGR.