The Top 5 Security Logging Best Practices to Follow Now
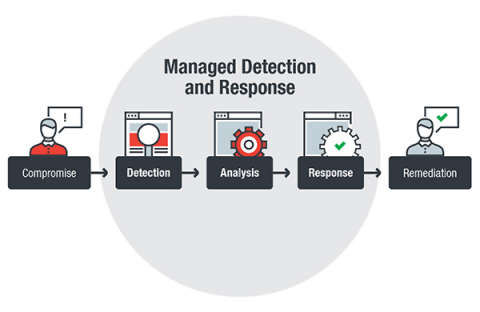
Security logging is a critical part of modern cybersecurity, providing the foundation for detecting, analyzing, and responding to potential threats. As highlighted by OWASP, security logging and monitoring failures can lead to undetected security breaches. With the average cost of a data breach adding up to $4.45 million, most organizations can’t afford to miss a security incident.