Why Organizations are Using Grafana + Loki to Replace Datadog for Log Analytics
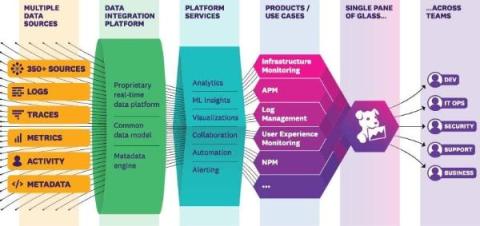
Datadog is a Software-as-a-Service (SaaS) cloud monitoring solution that enables multiple observability use cases by making it easy for customers to collect, monitor, and analyze telemetry data (logs, metrics and traces), user behavior data, and metadata from hundreds of sources in a single unified platform.