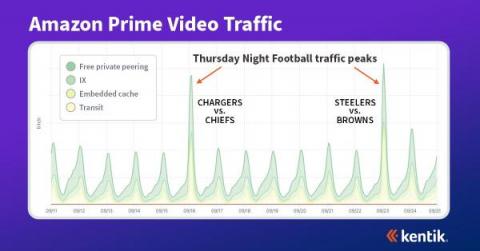
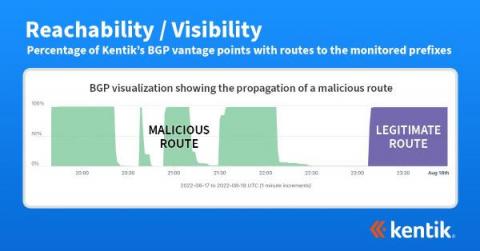
Flows vs. packet captures for network visibility
Recently, I saw some discussion online about how flow data, like NetFlow and sFlow, doesn’t provide enough network visibility compared to doing full packet captures. The idea was that unless you’re doing full packet captures, you’re not doing visibility right. Because I’ve used packet captures so many times in my career, I admit there’s a part of me that wants to agree with this.