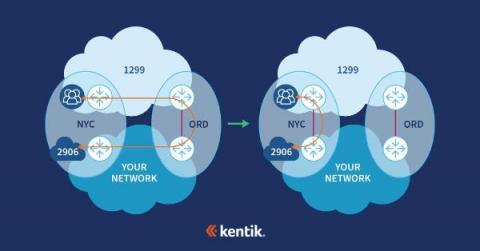
How New Relic uses Kentik for network observability
New Relic is known for empowering the world’s leading engineering teams to deliver great software performance and reliability. And the network that delivers that service to New Relic’s users plays a critical role. Hiccups in the performance of the network between New Relic’s mission-critical service and their users can create a cascade of problems.