Operations | Monitoring | ITSM | DevOps | Cloud
Splunk
Keeping Watch Over Microservices and Containers
Under the Hood With Splunk Observability
Network Observability for Distributed Services
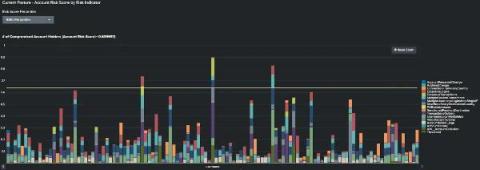
Using Maths to Fight Financial Crime
Financial crime has become a red-hot topic over the last 12 months, as fraudsters have sought to exploit the monitoring gaps between people, process and technology across an ever-widening attack surface – driven by the growth in usage of remote (digital) channels. Even before its recent growth, the cost of fraud and financial crime was significant.
How Can Companies Integrate Ethical AI? | Splunk's Ram Sriharsha & Dr. Rumman Chowdhury
Getting Started with the Splunk Distribution of OpenTelemetry Java
Splunk Distro for OpenTelemetry is a secure, production-ready, Splunk-supported distribution of the OpenTelemetry project and provides multiple installable packages that automatically instruments your Java application to capture and report distributed traces to Splunk APM (no code changes required!), making it easy to get started with distributed tracing!
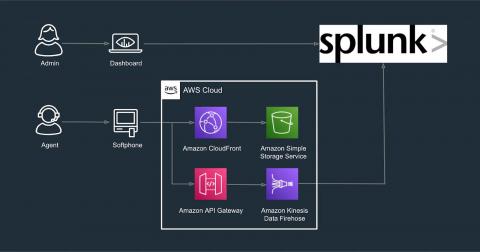
Splunk App for Amazon Connect: End-to-End(point) Visibility for an Optimal Customer Experience
How do you ensure a customer experience (CX) that leaves both participants of a conversation not just satisfied, but elated afterwards? And how do you do that, thousands of times over the course of a day and millions of times a year?
Splunk and Zscaler Utilize Data and Zero Trust to Eradicate Threats
The past year has challenged us in unimaginable ways. We kept our distance for the greater good, while companies faced the daunting task of transforming their workforce from in-person to remote — practically overnight. This presented a unique challenge for cybersecurity teams. How would they ensure employees retained access to critical data in a secure way? Working in the cloud has made remote work easier for many organizations, but has also presented new risks.
Streamlining Vulnerability Management with Splunk Phantom
Vulnerabilities are weaknesses in the security infrastructure that bad actors can exploit to gain unauthorized access to a private network. It is nearly impossible for security analysts to patch 100% of the vulnerabilities identified on any given day, but a vulnerability management plan can ensure that the highest risk vulnerabilities (those that are most likely to cause a data breach), will be addressed immediately.