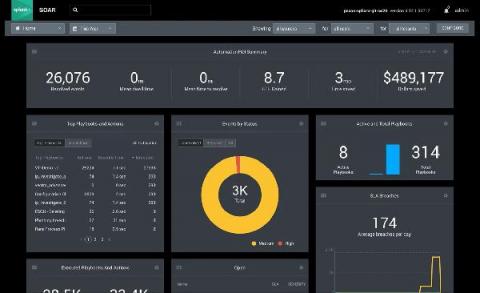
Introducing the World's First Modern Cloud-Based SecOps Platform: Splunk Security Cloud
To say that the past year presented its fair share of cybersecurity challenges to the InfoSec community would be a drastic understatement. The rapid migration to remote work at scale left 80% of CIOs unprepared, and SecOps teams struggled to confront the evolving threat landscape with disparate toolkits and skill sets. Not to mention that as more organizations shifted to hybrid and multi-cloud environments at scale, cloud complexity (and cloud-based threats) skyrocketed.