Operations | Monitoring | ITSM | DevOps | Cloud
Sumo Logic
5 Tips for Preventing Ransomware Attacks
You don't need to be a cybersecurity expert to know that ransomware attacks have become one of today's greatest IT security threats. From WannaCry to the attack against the city of Atlanta, major ransomware exploits have become so commonplace in the last few years that they may seem impossible to avoid. Fortunately, preventing ransomware is far from impossible. Let's take a look at a few strategies you can put in place to mitigate your risk of becoming part of the next ransomware statistic.
Tracking Malicious Activity across the Sumo Attack Lifecycle
Pokemon - Next Generation SOC From Theory to Practice
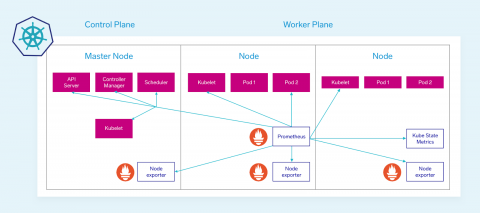
How to Collect Kubernetes Data
Now that we understand what machine data is available to us, how do we get to this data? The good news is that Kubernetes makes most of this data readily available, you just need the right tool to gather and view it. The solution we will discuss here heavily utilizes open source tools for collection and data enrichment because of their deep integrations and overwhelming community support.
Looker - A single source of truth in multi-source world
We Live in an Intelligence Economy - Illuminate 2019 recap
What a pleasure it was to see many of our customers at our Illuminate user conference, September 11-12. We had record attendance from customers, influencers, and partners. Our time was packed with keynotes, customer presentations (35 customer breakout sessions), certifications, sharing best practices, and time networking and having fun together.
Service Levels--I Want To Buy A Vowel
Everything old is new again–that’s a universal law! In our industry, we have talked about Service Level Agreements (SLAs) for a long time. At Sumo, we are proud to continue to be the only Machine Data Analytics Platform as a Service that commits to a query performance SLA.
Cloud Scale Correlation and Investigation with Cloud SIEM
Virtually every organization is a victim of cybercrime today. As the threat landscape evolves and proliferates, it’s necessary to prioritize the protection of data, customers’ privacy and brand reputation. Security directors must be prepared and equipped with the necessary tools to detect security events and address them accordingly at all times.