Operations | Monitoring | ITSM | DevOps | Cloud
Sumo Logic
Security Strategies for Mitigating IoT Botnet Threats
As DevSecOps continues to redefine the IT security landscape, security is becoming everyone’s responsibility. That means that staying ahead of the latest cybersecurity threats—such as IoT botnets—should be a priority for every DevOps professional. To help you do that, this article discusses strategies for combating IoT botnets.
How to Read, Search, and Analyze AWS CloudTrail Logs
In a recent post, we talked about AWS CloudTrail and saw how CloudTrail can capture histories of every API call made to any resource or service in an AWS account. These event logs can be invaluable for auditing, compliance, and governance. We also saw where CloudTrail logs are saved and how they are structured. Enabling a CloudTrail in your AWS account is only half the task.
Sumo Logic Helps ABinBev Modernize its Security Operations Center
Serverless vs. Containers: What's the Same, What's Different?
Containers and serverless computing are two of today’s hottest technologies for application deployment. When used the right way, they both help DevOps teams to deploy applications faster and more cost-effectively. Although the features of containers and serverless architectures overlap in some respects, they are not interchangeable technologies. Containers work better for some use cases, while in others, serverless is what you need.
How to Monitor Syslog Data with Sumo Logic
If you are reading this article, you’re probably familiar with syslog, a logging tool that has been around since the 1980s. It is a daemon present in most Linux-based operating systems. By default, syslog (and variants like rsyslog) on Linux systems can be used to forward logs to central syslog servers or monitoring platforms where further analysis can be conducted. That’s useful, but to make the very most of syslog, you also want to be able to analyze log data.
Know Your Logs: IIS vs. Apache vs. NGINX Logs
Today’s web server ecosystem has three big players: IIS, Apache and NGINX. Although only two of them (Apache and, to a lesser extent, NGINX) are cross-platform, it’s increasingly important to be able to work with all three of these servers, because you never know which type of operating system and web server platform you’ll be asked to support. That’s why understanding the nuances of IIS, Apache and NGINX logs is important.
Multi-Cloud Security Myths
As multi-cloud architectures grow in popularity, more and more organizations will start asking how to secure multi-cloud environments. Some will conclude that a multi-cloud architecture requires a fundamentally different approach to cloud security. That’s one example of a myth about cloud security in a multi-cloud architecture. Let’s take a look at why this assumption is flawed, along with some other common myths about multi-cloud security.
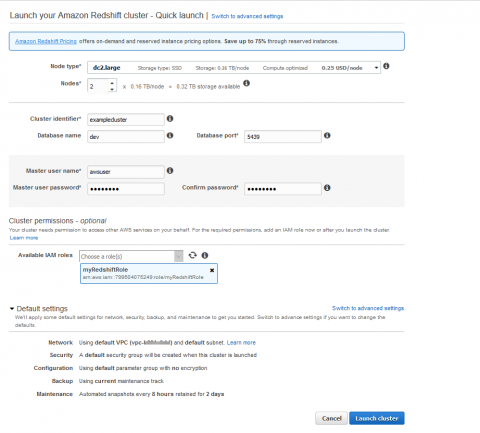
What is Amazon Redshift?
In this blog series, we will cover how Amazon Redshift and Sumo Logic deliver best-in-class data storage, processing, analytics, and monitoring. In this first post, we will discuss how Amazon Redshift works and why it is the fastest growing cloud data warehouse in the market, used by over 15,000 customers around the world. When an organization gains traction, the size of data that needs to be stored, monitored, and analyzed expands exponentially.
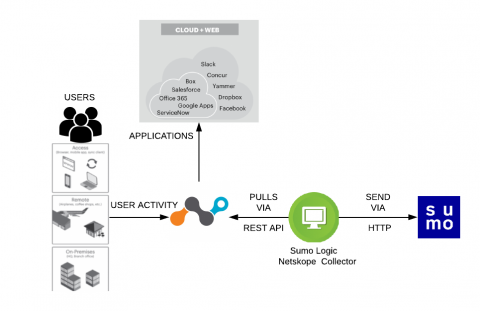
Sumo Logic adds Netskope to its Security and Compliance Arsenal
As the worldwide spending on SaaS spending will make up more than half of all public cloud services spending through 2019, it is critical to have end-to-end visibility into threats across your SaaS and on-premise applications. Sumo Logic and Netskope are collaborating on a technical integration that will help joint customers use Sumo Logic to correlate, validate and investigate Netskope alerts into their overall security incident investigation process and understand SaaS application usage patterns.