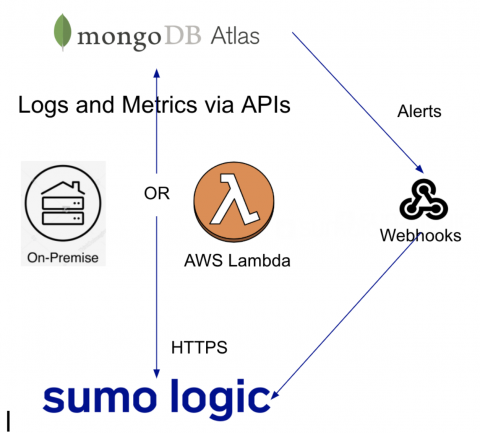
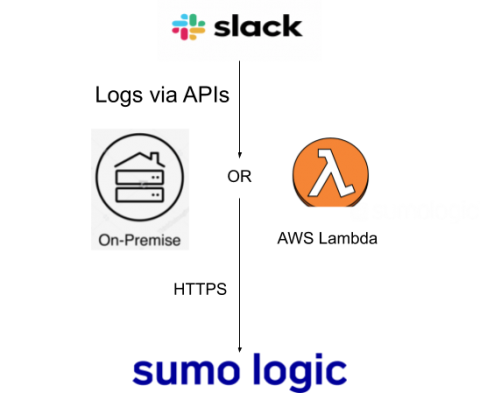
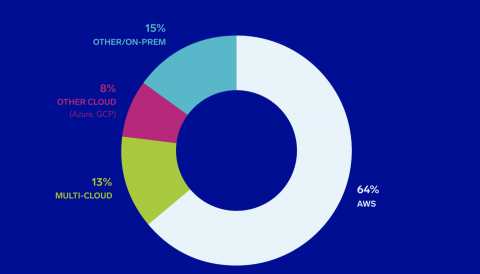
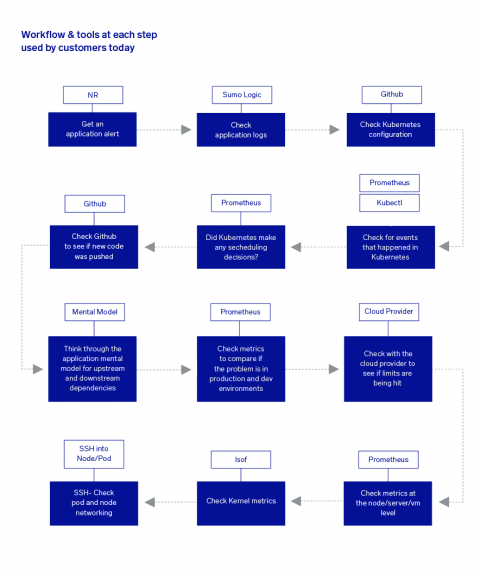
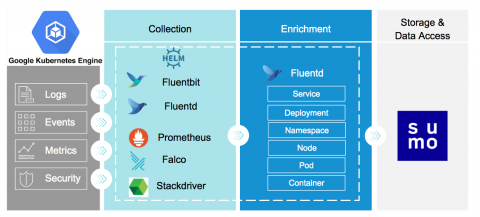
More Innovations from Sumo Logic that Harnesses the Power of Continuous Intelligence for Modern Enterprises
As a continuation of our latest innovations announcement at Illuminate, I want to take this time to announce a few other innovations we made in the past few months that allow our customers to maximize the use of our Continuous Intelligence platform to help them accelerate their pace of innovation and differentiate the services they deliver to their customers.