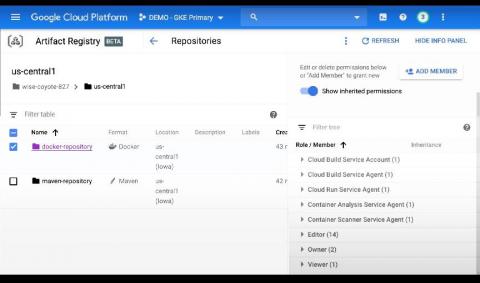
Sysdig extends image scanning to Google Cloud's Artifact Registry
In support of modern application development built on CI/CD, containers and open source, Google Cloud launched Artifact Registry (now generally available), a new artifact management solution. Sysdig helps DevOps teams using Artifact Registry confidently secure the build pipeline with comprehensive image scanning that identifies container vulnerabilities and misconfigurations to reduce risk.