German research organization bids adieu to multiple management platforms using OpManager
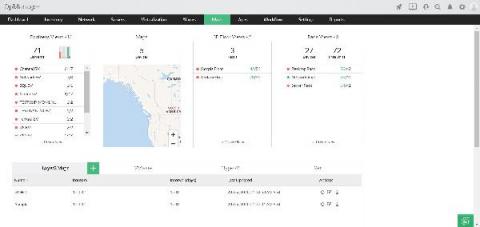
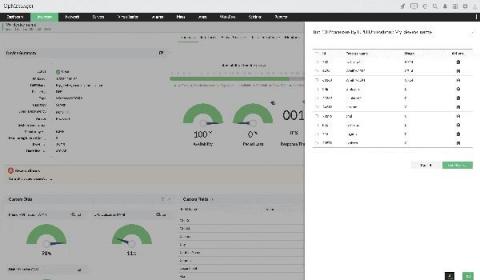
GFK is Germany’s largest market research institute and the fourth biggest market research organization in the world. It has a global digital presence in over 60 countries, with around 120 offices, and has been providing consumer and market insights for over 85 years. How OpManager helped GFK GFK struggled to find the right solution while managing its data centers and relied on too many management platforms.