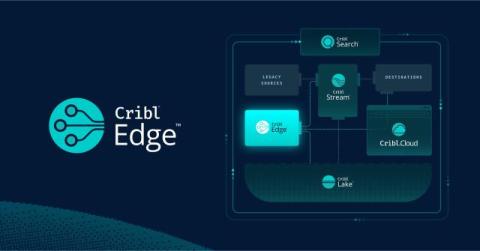
How to Slash Cyber Security Costs with Cribl Stream
Imagine the panic of a business owner who starts the day with a devastating realization: their entire database has been compromised, and the attackers demand a ransom that threatens the very survival of the business. Unfortunately, this isn’t just a nightmare what-if, it’s an all-too-common reality in today’s connected world.