5 Best Cloud-Based Monitoring Tools
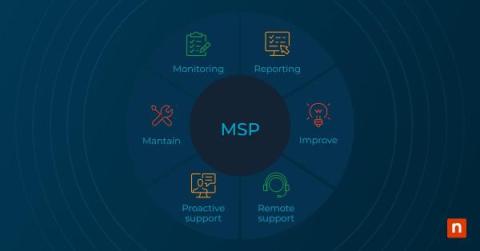
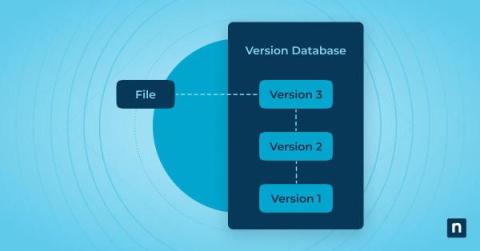
Rapid advancements in technology have welcomed the rise of cloud computing. This has changed how we access and manage IT resources, shifting the paradigm to more cloud-based management and monitoring. However, with so many moving parts, maintaining complete visibility and control can be a challenge. This is the hurdle that cloud-based monitoring tools are trying to overcome.