Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
SaaS vs. PaaS vs. IaaS: What's the Difference?
Every service you acquire to use temporarily and let go of when you’re done can use the “as a service” suffix. A cab is a vehicle as a service. Rather than buying a car, you merely pay to have another person’s car move you from one point to the next. IT services embody the same model. Browser-based text editors alleviate the need to install fully-fledged word processors on computers.
Terraform Cloud for deployment management
As we develop and deploy cloud compute automation and optimization solutions here at Spot by NetApp, we use various tools to improve our day-to-day operations. In this post I’ll share how we’ve found Terraform Cloud from Hashicorp to be quite helpful with deployment management.
AI on premise: benefits and a predictive-modeling use case
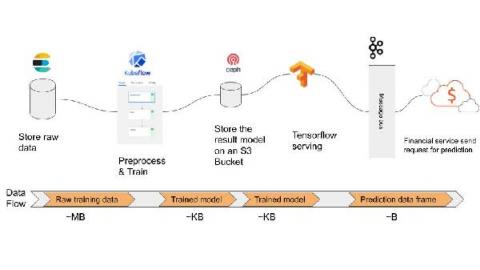
Running an Artificial Intelligence (AI) infrastructure on premise has major challenges like high capex and requires internal expertise. It can provide a lot of benefits for organisations that want to establish an AI strategy. The solution outlined in this post illustrates the power and the utility of the universal Operator Lifecycle Manager (OLM) using Juju, a universal OLM, to create and manage on premise AI infrastructure.
Analytics-Based Investigation and Automated Response with AWS + Splunk Security Solutions
Organizations are migrating an increasing amount of their infrastructure into the cloud. The cloud provides organizations with a number of benefits like greater scalability, improved reliability and faster time to value. However, these potential benefits can be offset if security is an afterthought.
Consumer broadband takes center stage - are CSPs ready?
It could be argued that consumer broadband networks have historically been poor neighbours of business networks, with CSPs investing more funds in providing better SLAs to their higher paying business customers. But like it did for many of our pre-set ideas, the pandemic turned the tables around for broadband priority. Forced work from home policies, remote learning, and quarantines have effectively turned consumer broadband into business/educational/health broadband services for many.
Idea 11 Customer Spotlight
In this first edition of our Customer Spotlight series, we are joined by James Kahn and Ben Gittins of Idea 11. Idea 11 is an award-winning, full-stack AWS IT company that specializes in digital transformations, cloud infrastructure, software development and managed services.
Secure Kubernetes by default with support for GKE Shielded Nodes on Ocean
Security remains a consistent priority for cloud providers to ensure that customers are always protected, data is secure and applications are safe. Users of Google Kubernetes Engine (GKE) are provided with ways to maintain the integrity of the compute instances that applications are running on top of.
IAM Policy Basics and Best Practices
One of the most powerful aspects of AWS is their Identity and Access Management (IAM) service. The obvious aspect of its power is that it controls who can do what with all the resources inside your AWS account. But the non-obvious side is how configurable it is. You can encode permissions that are so finely grained that a Lambda Function could, for example, be given just enough permissions to be able to read one attribute from one record for the current user of a DynamoDB Table.
What is cloud native?
The term cloud native is widely used when thinking about computing and software development, encompassing a wide range of concepts that are regularly used in technology. Let’s break it down and take a closer look – what does cloud native really mean?